Hacking—a word that inspires fear in internet and tech users everywhere. For as long as ‘technology’ has existed, so too has the ability to manipulate it for monetary gain, data collection, and general misuse.
Compared to the peak of the pandemic, where there were as many as 125 million breaches, hacking is clearly on a downward trend—there were approximately 52 million data breaches online in the most recent quarter. But 52 million data breaches is still 52 million too many.
Security cameras are as at risk as any other kind of internet-based technology. Thankfully, there are ways to minimize that risk. Read on to discover our tips on how you can protect your security camera from hackers, including specific guides for leading brands Ring, Wyze, Arlo, eufy, and AlfredCamera.
5 Tips to Prevent Security Camera Hacking
1. Consider Wired
Wired security cameras (in other words, conventional CCTV that interfaces with a DVR) are significantly less popular than the budget IP cameras taking the home security market by storm. Internet-enabled cameras are more affordable, more mobile, and packed with more useful features than their traditional wired predecessors.
Despite all that, it remains true that a totally wired security camera is more secure than a wireless one.
Of course, wired cameras can be ‘hacked’ like any other kind of electronic device, but assuming it has no internet functionality, this would essentially amount to cutting wires or stealing footage, meaning the hacker would need direct physical access to the network.
The internet, on the other hand, is a network accessible from anywhere in the world, meaning that vulnerabilities can be much more easily exploited to steal data.
Make no mistake: we love IP cameras and modern wireless technologies. It’s what we do, after all. But if you are looking for long term security solutions, particularly in larger businesses, it is worth considering wired alternatives and weighing up the pros and cons based on your specific needs should hacking be a major concern.
2. Reducing Data Sharing
When you set up your security camera, you’ll most likely have to create an account. Some brands may give you the option to skip this altogether. As you go through the onboarding process, you’ll be asked to agree to certain terms and conditions, while other things are optional, like sharing certain types of data with the company.
A wise thing to do, then, is to be conscious of what you are agreeing to as you set your device up. Some brands will require significantly more data than others.
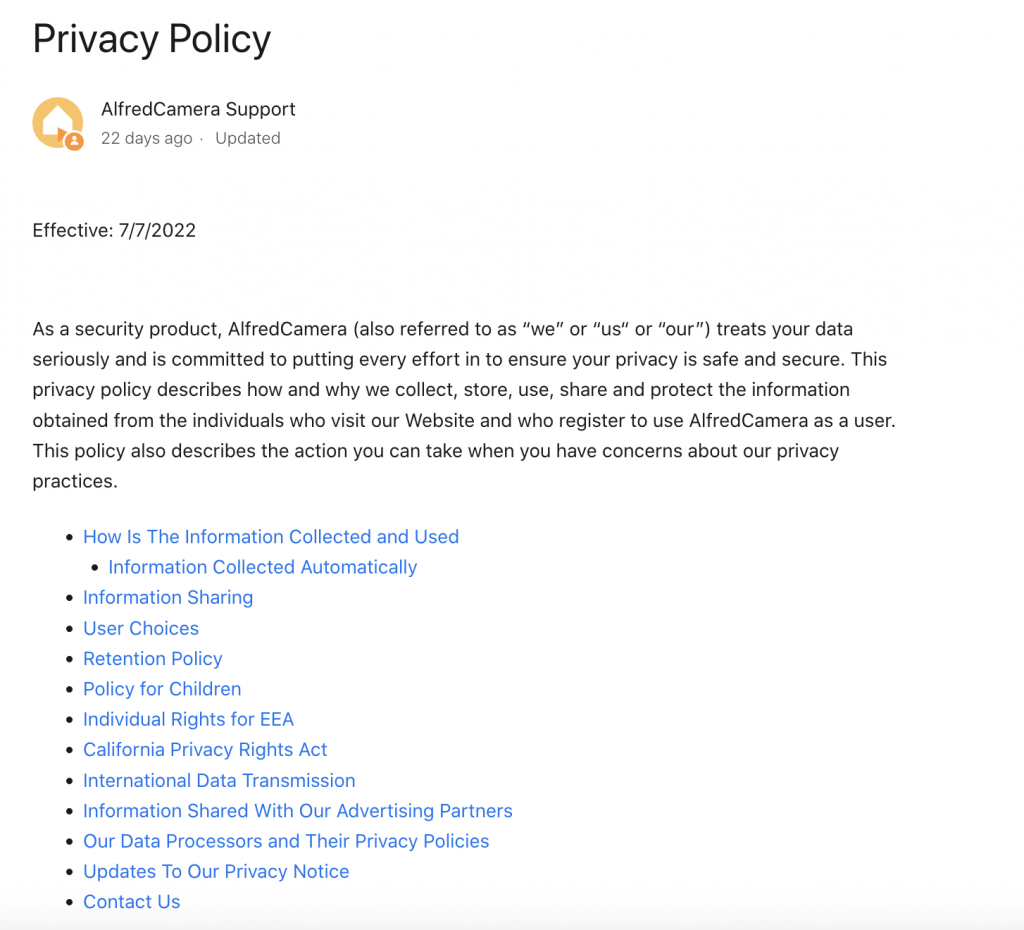
As you go through onboarding, consider minimizing how much you agree to share where possible. This minimizes the amount of data that can be accessed should vulnerabilities emerge and be exploited by hackers.
3. Reset Your Passwords!
Back in 2017, Hikivision, a company that owns about 40% of the surveillance and security camera market, suffered a huge cyberattack that put hundreds of millions of IoT devices at risk. This impacted a whole host of leading tech brands. The vulnerability in question? Passwords.
Users across the world started to notice they were being locked out of their DVR/NVR, and it was soon clear that passwords were being changed by bots. The users that were impacted all had the same default admin password: 12345.
We won’t chew your ear off here, because you’ve heard it all before–changing your passwords regularly really is fundamental to maintaining safety on the internet. Not only that, but passwords with a complex mixture of letters, numbers, and symbols are much safer than ‘password’ or ‘12345’.
Likewise, altering your passwords across products and services so that no two passwords are ever the same is highly encouraged.
4. Latest Firmware Updates
Another lesson learned from the Hikivision hacks relates to firmware. Vulnerabilities are uncovered on a daily basis; data breaches aren’t one-time things. They are constantly being attempted at extraordinary rates.
That’s why software updates are regularly rolled out for most products and services. Vulnerabilities that may present themselves can be patched in an update, which is then sent out to consumers.
The Hikivision breach was facilitated by a vulnerability on much older versions of the firmware than what was at the time the latest version. Aside from using the default ‘12345’ password, the affected users were also not using the latest firmware, but instead a much older version.
As was the case here, it’s not practical for companies to go back and revisit much older versions of software, as new software constantly has to be patched and updated. If your security camera suggests doing an update, do it immediately.
5. Don’t Freak Out
Most of us do not have such highly valuable data that warrants a targeted attack on our security cameras. This is absurdly costly, time consuming, and difficult to carry out. In a word, it’s extremely rare and unlikely to happen. Having a realistic understanding of the threat level can help you to remain level-headed about security risks.
Hacks are much more likely to be carried out in an attempt to steal financial assets (credit card numbers or other financial accounts details) than they are to gain access to your camera’s live feed. If this ever did happen, it would be quite easy to spot. Your camera would stop working properly, you might be locked out of your account, or the livefeed may not show up on your paired device.
Not to mention, it’ll be moving, making noise, and flashing its LEDs on its own. Respond accordingly: unplug the camera and contact the manufacturer. File a police report if they fail to take adequate and rapid responsibility.
In the event of a financial theft, banks are generally very responsive. If you notice an unusual transaction, you can contact them and have the card or account frozen and outbound payments canceled and restored.
Tips for Specific Brands
Leading security brands like Ring, Wyze, Arlo, Eufy, and AlfredCamera have specific means of protecting and encrypting user data, as well as their own terms and conditions. Some brands may require more data sharing than others, for example, and many of the leading brands have experienced data breaches in the last few years.
Read on to learn how to protect your devices, and find out about the recent data breaches that you should be aware of.
Protect your Ring cameras from being hacked
Back in 2020, a class action lawsuit was launched against Amazon’s Ring. Plaintiffs claimed that hackers threatened them with sexual assault and murder through their smart cameras.
Thankfully, Ring has pushed for much stronger security since then, rolling out end-to-end encryption on most of its devices, as well as two-factor authentication.

After the scandal, Ring now requires significantly less third-party data sharing. Still, there are some things that you have to provide consent for. In the Ring app, you can disable personalized advertising from the Control Center and opt out of third party-data sharing. In the Law Enforcement Privacy section you can also disallow Ring from sharing your videos with law enforcement.
Like many security camera providers, you can add shared users via the app from the settings menu. Tap Shared Users and Add User. Doing this is much more secure than sharing login information, which is a massive security compromise. Find out how to check and update your firmware here.
As was the case with the Hikivision, the Ring hack was facilitated through passwords. The hacker accessed the Ring accounts because the owners reused passwords from other platforms. Change passwords regularly, making complex passwords that never repeat existing ones.
Source:
https://www.theguardian.com/technology/2020/dec/23/amazon-ring-camera-hack-lawsuit-threats
https://www.digitaltrends.com/home/how-to-prevent-your-ring-smart-camera-from-being-hacked/
Protect your Wyze cameras from being hacked
Another victim of a pretty huge data breach was Wyze. The breach in question was initially reported by third party blogs in 2019 and then addressed by Wyze several months later. It reportedly affected all users that created an account before December 26th 2019, exposing millions of user names, emails, profile pictures, device names, and Wi-Fi router names, among other things, like health information of certain users.
Thankfully, passwords, financial data, and video files were not exposed.

Finger pointing at the users for this kind of data breach is pointless, since it is not facilitated through user error. Wyze has since hired an independent company to conduct penetration tests, added ‘report a security vulnerability’ tools, multi-factor authentication, and so forth.
On the users part, make sure to enable two-factor authentication through the Wyze app’s settings to increase your own security. Always install the latest firmware and app updates as soon as they become available so that you have the most up-to-date and secure software in use. Release notes for all firmware for all Wyze products can be viewed here.
Source:
https://learncctv.com/can-the-wyze-camera-be-hacked/
https://blog.12security.com/wyze/
https://forums.wyzecam.com/t/updated-02-13-20-data-leak-12-26-2019/79046
Protect your Arlo cameras from being hacked
At present, Arlo hasn’t suffered from a major security breach or a widespread hacking scandal. That’s likely thanks to its strong AES encryption, among other safety measures they take.
One blog did report that the Arlo base stations, Q, and Q Plus cameras have a vulnerability caused by factory default password (a vulnerability a lot of brands seem to have, including Ring). The window between the user first activating the device and making their own password is highly susceptible to being hacked, since the default password is easily identifiable.

New users must take care to immediately reset the password when prompted and not choose to keep using the default password if somehow able to. Instead, choose a complex password with a variety of letters, numbers, and symbols. Get into the habit of routinely changing it, and keep your app and firmware up-to-date.
Also, consider buying the Smart Hub add on, which securely connects your Arlo devices to the internet via your router (and allowing for local storage).
Source:
https://smarthomestarter.com/can-arlo-cameras-be-hacked-and-how-to-prevent-it/
https://community.arlo.com/t5/Arlo-Pro-2/News-coverage-this-week-on-inside-security-cameras-being-hacked/m-p/1745677
https://community.arlo.com/t5/Arlo/With-news-reports-of-Cameras-in-Australia-being-hacked-what-is/td-p/1779755
https://learncctv.com/arlo-security-breach/
Protect your Eufy cameras from being hacked
Last year, Eufy experienced its first privacy breach. Comparatively, it was a small breach, with only 0.001% of users impacted, and thankfully its impact was not global.
The cause was internal—purportedly, a software bug led to some users opening their apps to find other users’ livestreams and total access to their accounts. It was patched within a few hours.

Generally, Eufy’s supposed use of military-grade hardware, emphasis on local storage over cloud, and strong data encryption make it well regarded for safety and privacy. Users should make sure to only ever allow other users access to their paired devices via the app’s sharing feature rather than sharing login information in person. Opting out of cloud storage in favor of local microSD card storage will also significantly reduce risk.
Source:
https://smarthomestarter.com/can-eufy-cameras-be-hacked-are-they-safe/
https://www.makeuseof.com/eufy-urges-users-log-out-reset-cameras/
Protect your AlfredCamera device from being hacked
AlfredCamera puts a massive emphasis on privacy and user data protection, making extensive use of security mechanisms like W3C, HTTPS, and OAuth2 sign on. No passwords are ever stored on AlfredCamera servers, and URLs are always randomized. AlfredCamera has never experienced a data breach or widespread hacking incident.
Among its more unique safety precautions designed for users is the App Lock feature. When enabled, the app screen will lock after one minute of inactivity or thirty seconds of running in the background, preventing access to all Viewer and Camera devices. A PIN code must be entered to regain access. This helps protect your data should someone gain physical access to your device.

Activate two-step authentication for stronger security, and consider getting into the habit of checking the Device Management menu in the app to ensure no unusual devices have been linked. If they have, you can remove them immediately.
You can learn more about how AlfredCamera secures your data here.
What’s the Difference Between Hacking and Data Breach?
Hacking and data breaches are similar in that they both result in (illegal) access to someone else’s data through certain exploitable vulnerabilities in software, but they are not the same thing.
Hacking is when a targeted attack is made on one or multiple devices in order to gain access to it. This is usually facilitated through some kind of technology that exploits weak passwords or loopholes in other security techniques.
In the context of security cameras, a hacker may target Cloud-based storage services to gain access to footage saved on the internet, the camera itself to gain access to livestream footage, or to user accounts to steal financial details or other sensitive information.
A data breach, on the other hand, is usually caused by the company itself. A software bug, loophole, or hardware failure results in customer information being easily accessed, whether that’s intentional or by accident. It may then become publicly accessed or published online, whether mistakenly or through the actions of an individual looking to exploit the data.
In the context of security cameras, data breaches usually reveal personal information about customers, like addresses, names, and information about their internet connection. A data breach doesn’t enable direct access to cameras. Data breaches can potentially impact millions of users at once, whereas a hack is much more limited in its scope.
No security camera in existence is 100% secure against a hacking incident. Most targeted individual hacks will be done through a poor password, which does not require especially sophisticated technology to steal.
FAQ
How do security cameras get hacked?
Security cameras are hacked locally (in person) or remotely (over the internet or another network). Local hacking is extremely uncommon, as it requires direct access to the camera or network it is connected to. Unless achieved by guessing a particularly poor password, targeted remote hacks are very expensive to facilitate. Remote hacks will usually exploit certain vulnerabilities in the camera’s firmware (a type of software the camera uses to run) which the manufacturer has failed to patch.
What security cameras cannot be hacked?
No security camera is 100% safe from hacking. Minimizing the chances of being hacked are largely dependent on regularly changed, complex, and unique passwords, as well as keeping your camera’s firmware and app up to date.
How to tell if your security camera has been hacked?
Security camera hacks are quite difficult to conceal. You will notice your camera’s status LED is on when it shouldn’t be, and if the camera can pan or rotate, it may start to do this without your input (make sure to disable motion tracking to check this). You may also find yourself locked out of your own account. Less obvious symptoms will be increased network traffic–you might notice spikes at odd times, for instance–and altered settings that you didn’t enable.
Can hackers see you through your phone camera?
As with any kind of technology, it is perfectly plausible that a hacker could gain access to your front facing camera. But as with most scenarios, it is also extraordinarily unlikely to ever happen to you. That isn’t to say reports of celebrity phone hacks are untrue, but they are done precisely because there is money to be made off of doing so. A targeted attack of this nature is sophisticated and costs a lot.
For the rest of us, avoid using public Wi-Fi, which is always much less secure than home networks. To learn more about making your iPhone devices safe, read our guide on iOS security.
Can wired security cameras be hacked?
Yes, wired security cameras can be hacked. This is far more likely if the camera, despite being wired, has features that require an internet connection (e.g. the option for Cloud storage rather than DVR interfacing). Traditional wired security cameras with no internet functionality are much harder to hack because they require direct access to hijack.
Conclusion
Hacking is a scary prospect, security camera hacking even more so. But we prefer to advise logical caution over unfounded hysteria, and the reality is that even with a significant increase in data breaches at major security solutions providers, targeted hacking remains a pretty unlikely scenario for the vast majority of us.
The possibility of data breaches should be a far greater concern to consumers. This is far more likely to reveal the type of information bad actors are looking for: personal details and financial information.
Being aware of the companies that have experienced data breaches, and what kind of response they mounted in the aftermath, should provide some peace of mind.
